Most webhook scanning campaigns run from throwaway VPS instances. This one came from a full Kubernetes cluster with Envoy service mesh. Censys data showed consistent infrastructure across all source IPs—container orchestration, not opportunistic scanning.
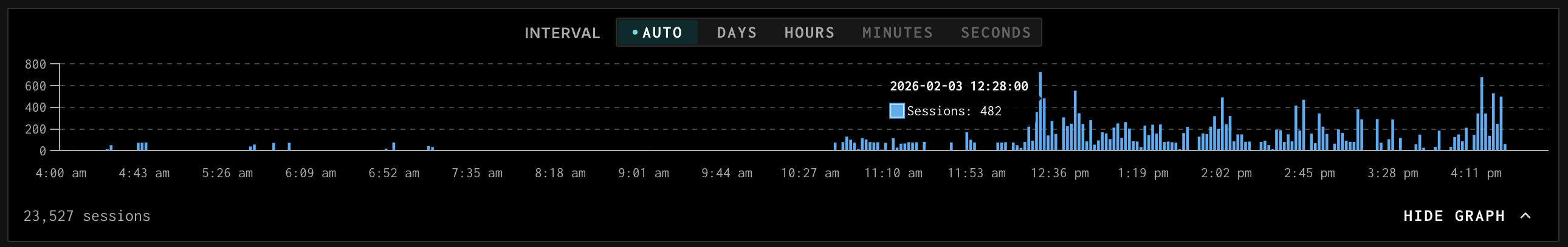
Between January 27 and February 3, 2026, the GreyNoise Global Observation Grid tracked 33,270 HTTP requests targeting webhook endpoints. The traffic originated almost entirely from AS211590 (Bucklog SARL), a French hosting provider, concentrated in the 185.177.72.0/24 subnet. The campaign probed for vulnerable webhook implementations with a particular interest in file upload paths, document processing endpoints, and—notably—n8n workflow automation platforms via CVE-2026-21858.
Campaign snapshot
| Attribute | Value |
|---|---|
| Total sessions | 33,270 |
| Time range | Jan 27 – Feb 3, 2026 |
| Primary ASN | AS211590 (Bucklog SARL) |
| Traffic share | 97.4% from single /24 subnet |
| Dominant user agent | curl/8.7.1 (97.4%) |
| HTTP method split | POST 95.9%, GET 4.1% |
| Peak activity | 70% within 2-hour window |
The Kubernetes twist
Censys lookups on the top 10 source IPs returned consistent Kubernetes infrastructure across all nodes:
| Port | Service | Present on |
|---|---|---|
| 10250 | Kubelet API | 10/10 IPs |
| 10256 | kube-proxy health | 10/10 IPs |
| 9964 | Envoy proxy | 10/10 IPs |
| 32362 | NodePort | 5/10 IPs |
All nodes run Debian 12 “Bookworm” with OpenSSH 9.2p1. The Envoy proxy presence indicates a service mesh deployment—likely Istio, Linkerd, or Consul Connect.
Operational implications:
- Rapid scalability. Containerized scanning tools deploy and destroy in seconds across 375+ IPs.
- Cost efficiency. Short-lived containers minimize infrastructure costs.
- Operational security. Container isolation complicates attribution and forensics.
- Multi-campaign support. A single cluster can run multiple concurrent scanning operations.
The exposed kubelet API on port 10250 is worth noting—if unauthenticated, it enables full node compromise. Whether Bucklog SARL is aware their infrastructure is being used this way remains an open question.
Attack methodology
Dictionary-based path enumeration with uniform request distribution: 67-69 requests per path across the target set. Automated tooling cycling through a predefined wordlist.
Top probed paths:
/webhook/upload/webhook/api/file/webhook/backup/webhook/import/webhook/internal/import/webhook/admin/upload/webhook/documents/webhook/blob/webhook/storage
Pattern: file upload, document processing, and administrative import functions—paths most likely to accept arbitrary file uploads or expose path traversal vulnerabilities.
n8n CVE-2026-21858 targeting
Forty sessions used a n8n-scanner/1.0 user agent—a specialized tool for probing n8n workflow automation platforms. The campaign targeted CVE-2026-21858, an arbitrary file access vulnerability in n8n webhook handlers that allows path traversal via malformed multipart/form-data requests.
Attack samples showed rapid-fire sequencing (one request per second) against n8n-specific endpoints:
/webhook/internal/import/webhook/user/upload/webhook/admin/upload/webhook/admin/import/webhook/bulk/webhook/v1/files
The /proc filesystem probing (28,756 tag hits for “Generic /proc Enumeration Attempt”) suggests post-exploitation planning. Successful path traversal would enable access to /proc/self/environ (environment variables), /proc/self/cmdline (command-line arguments), and /proc/net/tcp (network connections)—all useful for credential harvesting and lateral movement.
Tooling signatures
Consistent tooling fingerprints across 95%+ of traffic:
JA4H HTTP fingerprints:
| Fingerprint | Sessions | Share |
|---|---|---|
po11nn16enus_6291b5733205_... |
15,135 | 45.5% |
po11nn17enus_4eb89d0aaebb_... |
13,631 | 41.0% |
Two curl variants account for 86.5% of traffic. The po11 prefix indicates POST requests with 11 header fields—consistent with curl defaults.
JA4T TCP fingerprint:
The dominant fingerprint appeared in 95.9% of sessions and maps to Linux kernel 4.x+ with default curl TCP stack behavior and standard Ethernet MTU.
JA4T 95.9% consistency + curl 97.4% coverage = minimal tooling diversity across the IP range. It’s almost certainly the same actor, using the same infrastructure and same exact tooling.
Temporal pattern
Activity concentrated in a narrow window on February 3:
- 13:00–14:00 UTC: 3,496 sessions (70%)
- 14:00–15:00 UTC: 1,504 sessions (30%)
Coordinated infrastructure spinup at 13:00 UTC, peak operations in the first hour, controlled teardown. Ephemeral container deployments minimize operational footprint and cost.
Attribution assessment
Confidence: Medium
| Signal | Assessment |
|---|---|
| Infrastructure | Kubernetes cluster with service mesh (not opportunistic VPS) |
| Tooling | Consistent curl + specialized n8n scanner |
| Geographic concentration | 100% France, single ASN |
| Temporal coordination | 2-hour burst indicates orchestration |
Three scenarios:
Adversary-rented Kubernetes infrastructure (most likely). Threat actor renting Bucklog’s Kubernetes-as-a-Service for scanning operations. The service mesh deployment indicates sophisticated container orchestration.
Compromised customer cluster (less likely). A Bucklog customer’s Kubernetes deployment weaponized by attackers. The exposed kubelet API makes this possible, but the professional deployment suggests intentional setup.
Bucklog internal operations (highly unlikely). Contradicted by malicious tag classifications and unlikely operational practices.
Indicators of compromise
Network indicators:
| Type | Values |
|---|---|
| Primary ASN | AS211590 (Bucklog SARL) |
| Subnet | 185.177.72.0/24 |
| Secondary ASN | AS16509 (Amazon AWS) |
| Primary user agent | curl/8.7.1 |
| Specialized tool | n8n-scanner/1.0 |
Targeted paths:
/webhook/upload,/webhook/api/file,/webhook/import/webhook/admin/upload,/webhook/internal/import/webhook/v1/*,/webhook/v2/*
Defensive recommendations
Immediate actions:
- Block AS211590 at the perimeter, specifically 185.177.72.0/24.
- Audit webhook implementations for path traversal vulnerabilities.
- Patch n8n installations against CVE-2026-21858.
- Monitor for
n8n-scanner/1.0user agent.
Detection rules:
- Alert on POST requests to
/webhook/*paths exceeding 50 requests/hour from a single source. - Flag curl user agents systematically probing file upload endpoints.
- Monitor for
/proc/filesystem references in HTTP request paths.
Webhook hardening:
- Implement strict input validation on multipart/form-data uploads.
- Require authentication on administrative webhook endpoints.
- Rate-limit webhook endpoints per source IP.
- Isolate webhook handlers with restricted egress.
What’s next
The reconnaissance phase appears complete. Based on historical attack progression, we expect exploitation attempts within 7–14 days targeting any vulnerable endpoints identified during this sweep.
We’re continuing to track AS211590 for emerging campaigns. The Kubernetes infrastructure suggests this operator isn’t going anywhere—the cluster likely supports multiple concurrent scanning efforts beyond webhook targeting.
If you’re running n8n in production, now’s the time to audit those webhook configurations. The scanner already knows where to look.