We were engaging in some routine clustering on untagged or only-generically-tagged HTTP traffic when a fun pattern jumped out: thousands of requests hitting /wp-content/plugins/*/readme.txt. It doesn’t take a cybersecurity wonk to come to the conclusion that this is basic WordPress plugin enumeration. The reason this stood out is that it showed up under the generic “Web Crawler” tag (and, only that tag), meaning we don’t currently classify this as the enumeration that it is. While we’re working on said tag, let’s take a look and what the last ~90 days of activity can tell us about opportunistic attackers and their penchant for hunting for insecure WordPress installations.
If you’re pressed for time, the TL;DR is we found a combination of coordinated reconnaissance infrastructure, single-actor mass scanning events, and ~90 IPs that do nothing but hunt for one specific plugin.
If not, read on to learn about the suspicious Sri Lankan spike, persistent plugin pokers, and monagamous mail marauders!
The setup
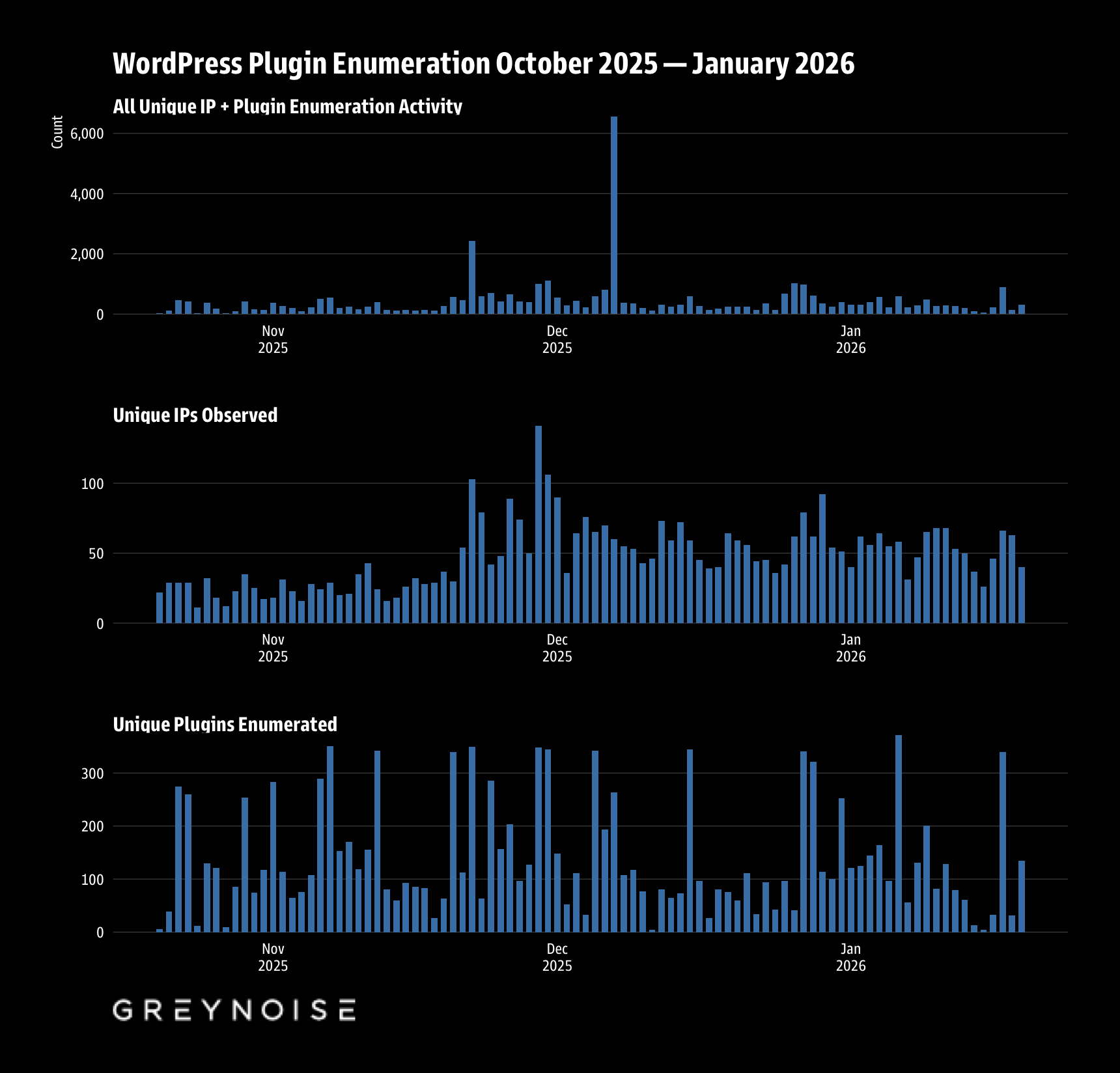
Our Global Observation Grid (GOG) captured 40,090 unique WordPress plugin events between October 20, 2025 and January 19, 2026. “Unique”, here, means a unique combination of day, source IP, and targeted plugin (many engage in multiple sessions across the fleet, so the total activity is ~91K events).
Here’s what we were working with:
| Metric | Value |
|---|---|
| Unique Source IPs | 994 |
| Unique ASNs | 145 |
| Unique Plugins Targeted | 706 |
| Unique JA4T Fingerprints | 84 |
| Unique JA4H Fingerprints | 131 |
| Median Daily Records | 282 |
| Peak Daily Records | 6,550 |
That peak day deserves its own section, which we will get to short order.
Not all plugins attract equal attention, so we also ranked targets by two dimensions: persistence (how many days they were scanned) and volume (how many unique IPs probed them).
| Plugin | Days Observed | Unique IPs |
|---|---|---|
post-smtp |
92 (100%) | 190 |
loginizer |
77 (84%) | 136 |
litespeed-cache |
74 (80%) | 135 |
seo-by-rank-math |
71 (77%) | 135 |
elementor |
75 (82%) | 107 |
duplicator |
71 (77%) | 94 |
We’ll take a look at somee of them, below, and the complete ranked list with additional data files is available at https://github.com/GreyNoise-Intelligence/gn-research-supplemental-data/tree/main/2026-01-19-wordpress-plugin-enumeration.
Mail call!
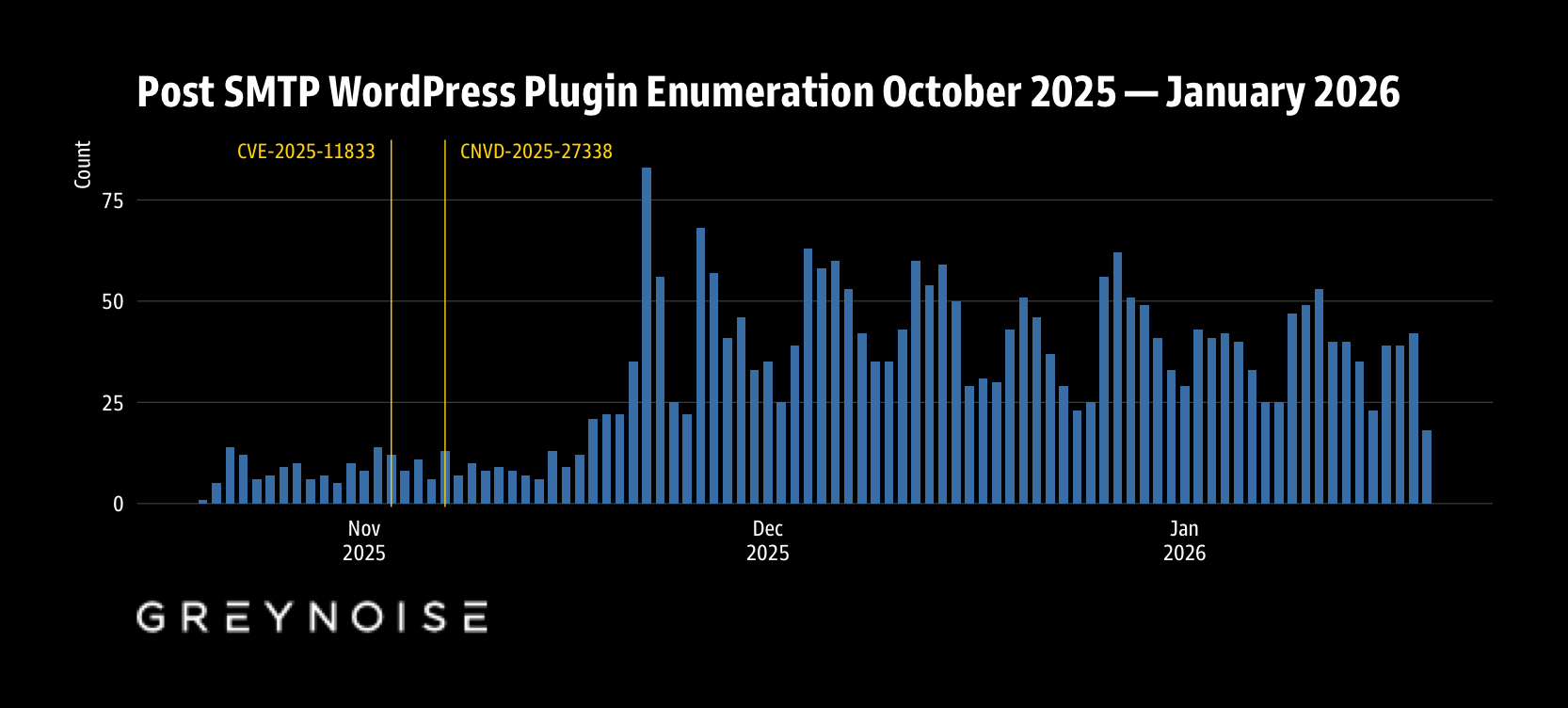
post-smtp — a “a free, next-generation WordPress SMTP plugin that improves email deliverability for your WordPress site” — showed up Every. Single. Day of the observation window, so it’s pretty clear that the SMTP handshake brings all the bots to your yard.
Accorting to Vulnerability Lookup, it has its fair share of CVEs, and one was published “shortly” before the extra burst in activity seen on the chart (above). There are two markers for it since it hit China’s national vulnerability database a short while after the CVE was published. There may be no causal relationsihp, but this is a pretty nasty bug — “Missing Authorization to Account Takeover via Unauthenticated Email Log Disclosure” — which would be an ideal candidate for extra special attention.
When we segmented IPs by behavior, 91 addresses fell into a “single-plugin specialist” category, meaning that they scan for exactly one plugin and nothing else. So, yep!…all 91 exclusively target post-smtp.
Rather than the usual opportunistic vulnerability scanning, this represents a coordinated campaign focused on email infrastructure. Post SMTP Mailer handles SMTP configuration for WordPress sites, so when attackers comprimise it, they abuse your high reputation mail sender to deliver spam and phishing messages.
Cache me if you can
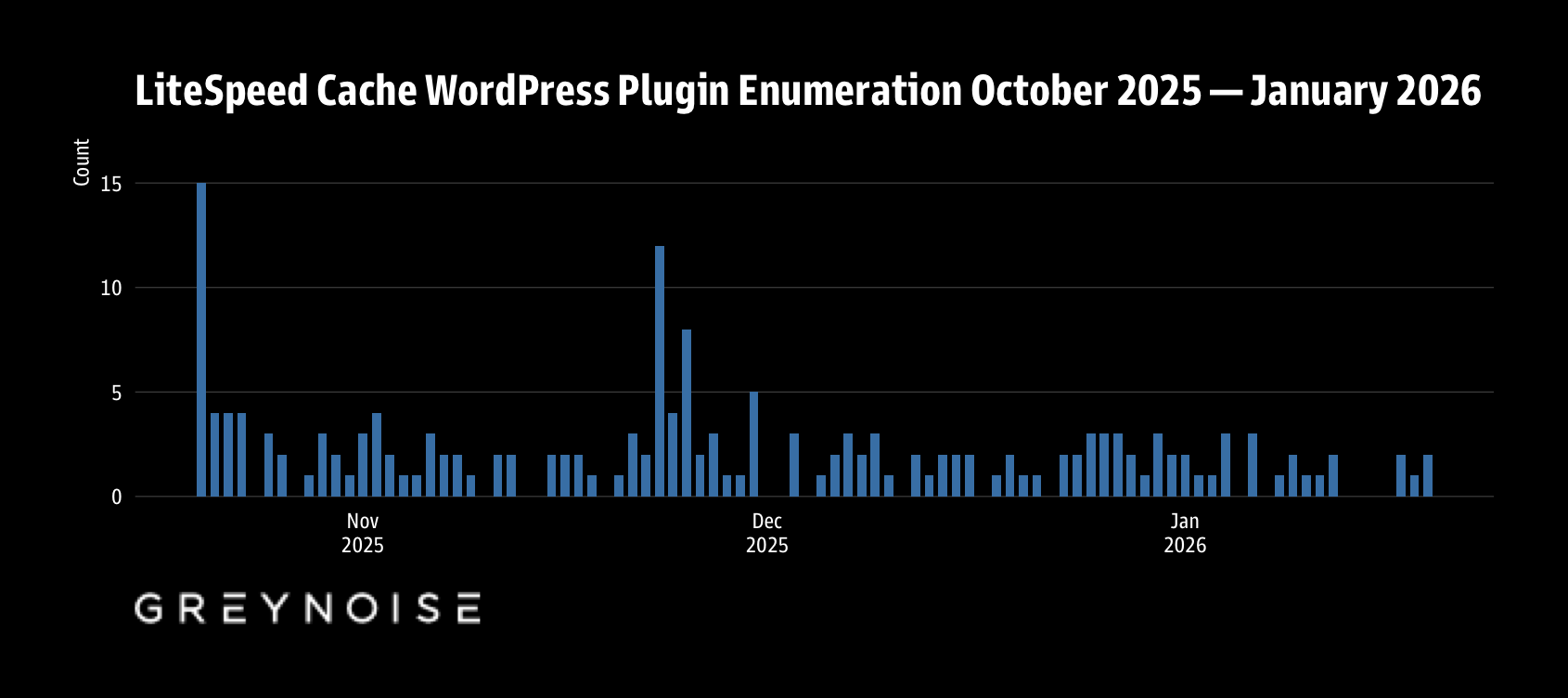
LiteSpeed Cache sits on over 7 million WordPress installations and has a small but decent corpus of CVEs to call its own. CVE-2025-12450 popped on the scene the same day as that spike-y initial bar on the chart (above). But, it’s “just” a reflected cross-site scripting weakness, so I suspect it’s not the real reason for that observation being larger than the rest.
It does have a solid number of near-perfect-score CVEs, and attackers may just be fighting for control of that substantial server population.
Interlude: Who’s doing the scanning
If you’ve been with us for a while, you know that infrastructure always tells a story, so let’s take a peek at where the majority of this traffic originates:
| ASN | Organization | Unique IPs | Notes |
|---|---|---|---|
| AS13335 | Cloudflare | 125 (13%) | CDN/proxy infrastructure |
| AS135377 | UCLOUD HK | 123 (12%) | Coordinated cluster |
| AS63949 | Akamai/Linode | 116 (12%) | 92 days active |
| AS211680 | NSEC Portugal | 84 (8%) | VPS infrastructure |
| AS14061 | DigitalOcean | 32 (3%) | Cloud infrastructure |
With 123 IPs from a single ASN — many sharing identical JA4H fingerprints — the UCLOUD Hong Kong cluster caught our attention. They’re on our bulletproof hoster watch list, so it’s not really a surprise they’re in the mix.
Akamai/Linode showed up every single day of the 92-day window, so one or more actors is running persistent reconnaissance from that network.
JA4 fingerprints let us cluster actors by their TCP and HTTP characteristics. Two signatures dominated:
JA4T (TCP): - 65495_2-4-8-1-3_65495_7 — 381 IPs. Jumbo frames and custom MTU settings. Unusual. - 64240_2-4-8-1-3_1460_7 — 300 IPs. Consistent with WSL Ubuntu 22.04.
JA4H (HTTP): - The ge11nn040000_* family dominated scanning traffic across multiple ASNs.
Seeing the same JA4H fingerprint across different ASNs suggests shared tooling or malware family. Different JA4H from the same IP (we saw this during the December spike) suggests evasion attempts or multi-tool deployment.
So, about that spike…
On December 7, 2025, daily activity exploded to 6,550 unique sessions (🎗️ day + IP + plugin). That’s 23x the median. (We triple-checked this wasn’t a data issue.)
And, one IP drove 96% of it:
| Attribute | Value |
|---|---|
| Primary IP | 112.134.208.214 |
| ASN | AS9329 (Sri Lanka Telecom) |
| Records | 6,303 of 6,550 |
| Plugins Scanned | 334 |
| JA4H Fingerprints Used | 4 variants |
| Days Active | 2 (Dec 5 and Dec 7 only) |
This actor scanned 334 unique plugins in two days using four distinct HTTP fingerprints. Then they disappeared. Poof. It could just be aggressive reconnaissance or vulnerability scanner testing, but — either way — the behavior stands out.
A secondary spike on November 22 showed different characteristics: 2,440 records distributed across 103 IPs and 15 ASNs. More distributed, less dominated by a single actor. M247 Europe led that one with 1,595 records from a single IP.
WordPress weekend warriors
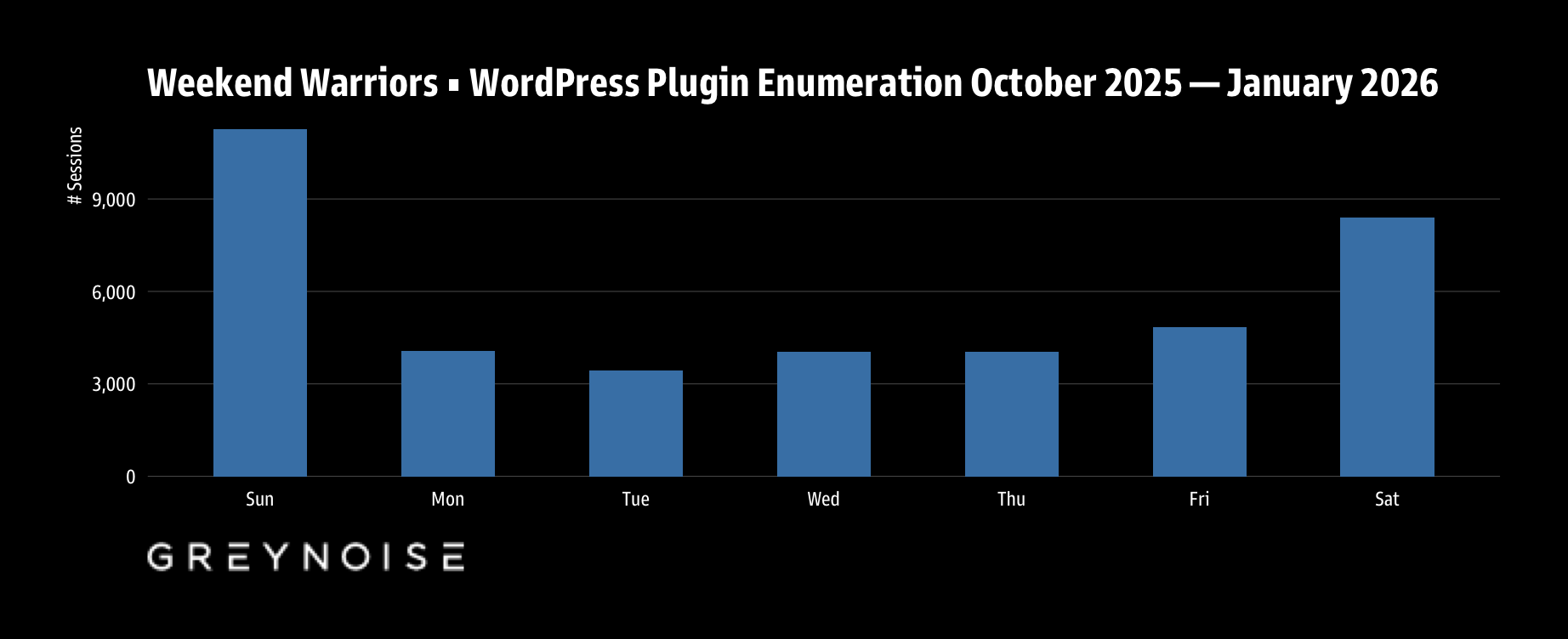
We noticed higher activity on weekends and decided it was worth a brief mention.
| Period | Avg Daily Records |
|---|---|
| Weekend | 756 |
| Weekday | 310 |
Weekend activity runs 2.4x higher than weekdays. This strongly suggests automated operations—scheduled scans timed for when security teams have reduced coverage. Human-operated campaigns typically show the opposite pattern.
Behavioral segmentation
We also classified IPs by their scanning behavior:
| Segment | Count | Behavior |
|---|---|---|
| Moderate Scanner | 370 | 2-10 plugins, moderate persistence |
| Single-Plugin Opportunist | 346 | One plugin, low persistence |
| Burst Multi-Plugin | 152 | Many plugins, short timeframe |
| Single-Plugin Specialist | 91 | 100% target post-smtp only |
| Mass Scanner | 32 | High volume, comprehensive enumeration |
The 32 mass scanners generate disproportionate noise. The 91 single-plugin specialists represent focused, likely coordinated activity.
Persistent infrastructure
29 IPs maintained activity for 30+ days, so the complete opposite of what one would epect from drive-by scannersh. Most came from dedicated reconnaissance infrastructure in Akamai/Linode (AS63949) and OVH (AS16276).
What we’re doing about it
This analysis is groundwork for a new WordPress Plugin Enumeration tag in GreyNoise since the current “Web Crawler” label is far too generic for this activity pattern, and you may like populating the raw_data.http.path field in our GNQL query expressions, but I definitely do not.
This forthcoming new tag will let you:
- Filter plugin enumeration from general crawler noise
- Track which plugins are being targeted in your traffic (the paths are in the API responses)
- Correlate with CVE timelines for emerging threats
Recommendations
If you run WordPress:
Why?!
Patch priority: LiteSpeed Cache (CVE-2024-28000), Post SMTP Mailer, Loginizer. These attract sustained attention.
Plugin audit: Cross-reference your installed plugins against the top-targeted list. Remove anything you’re not actively using.
Email infrastructure review: The post-smtp targeting suggests adversary interest in email compromise. Check your SMTP configurations.
If you’re hunting threats:
JA4 alerting: Flag
65495_2-4-8-1-3_65495_7(unusual jumbo frame signature) and thege11nn040000_*HTTP fingerprint family.Weekend coverage: Increase monitoring during weekends when automated scanning peaks.
Watch these networks: AS135377 (UCLOUD HK) for coordinated clusters, AS9329 (Sri Lanka Telecom) for aggressive single-actor campaigns.
What’s next
We’re continuing to monitor plugin enumeration patterns and will update this analysis as new campaigns emerge. The WordPress Plugin Enumeration tag should be live soon.
Questions or seeing similar patterns? Let us know!