Introduction
Hi there! I’m one of the researchers at Greynoise. While on the main blog I try to write formally, expect my blog posts in the Grimoire to be a little more off the cuff.
Over the course of our work, we get a lot of fresh, famous and common vulnerabilities tagged thanks to a combination of security news, vendor updates, CISA KEV updates, and private collaboration with security researchers and vendors.
These methods are excellent for writing up-to-date tags for the most relevant security vulnerabilities, but what happens when someone is trying older or more rare vulnerabilities? Or if someone is trying an exploit with no public documentation?
In those cases, we have to do a little digging ourselves. In this blog post, I’ll pull the curtain back a little bit on how we find and tag on less popular internet traffic.
There’s gold in them there hills
As of this blog post, we’ve got thousands of sensors emulating a huge number of different appliances, servers and other pieces of internet-connected software. There’s a lot to go through! I’m going to let you in on a little secret: sometimes, when I’m bored, I like to take a lucky dip into the sensor logs, turn my front end to full-screen mode, and pretend I’m reading the source code in The Matrix: Blonde, red dress, attacking Fortinet. When I want to be a little more productive, though, we’ve got a tool for that that we’re using internally pending a public release: Sift.
(psssst, we have a preview edition of Sift that shows items older than 1 week that you can play with here)
Sift looks through the logs sent by our sensors, looks for anything weird, then makes a report about the weird thing it found so we can tag it. If we’re panning for gold, then Sift is the pan after you’ve run the rocks and dirt through a screen.
Let’s look at Sift and make a tag from it!
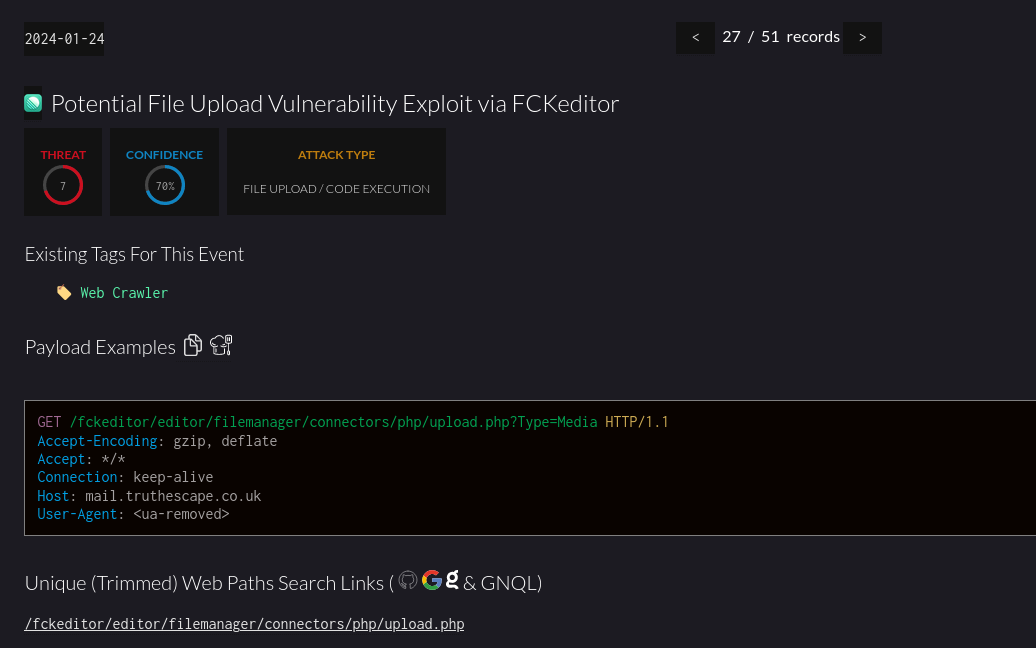
Here, we can immediately see a few key items:
- The payload itself
- The confidence level that this payload is what the heading says it is (the headings are automated)
- Any existing tags that match that payload
It’s helpful to have a lot of side information included on these pages. For example, the “existing tags” links have saved me a LOT of time doing research on something that is ultimately already tagged. Usually, though, I focus on the HTTP payload. The game has now changed from “find strange traffic for something we haven’t tagged yet” to “here is strange traffic that we haven’t tagged yet. What is it doing?”
What the dog doing?
There’s more than one way to figure this out, but I’ll just start with the easiest: a search that contains parts of the path being exploited.
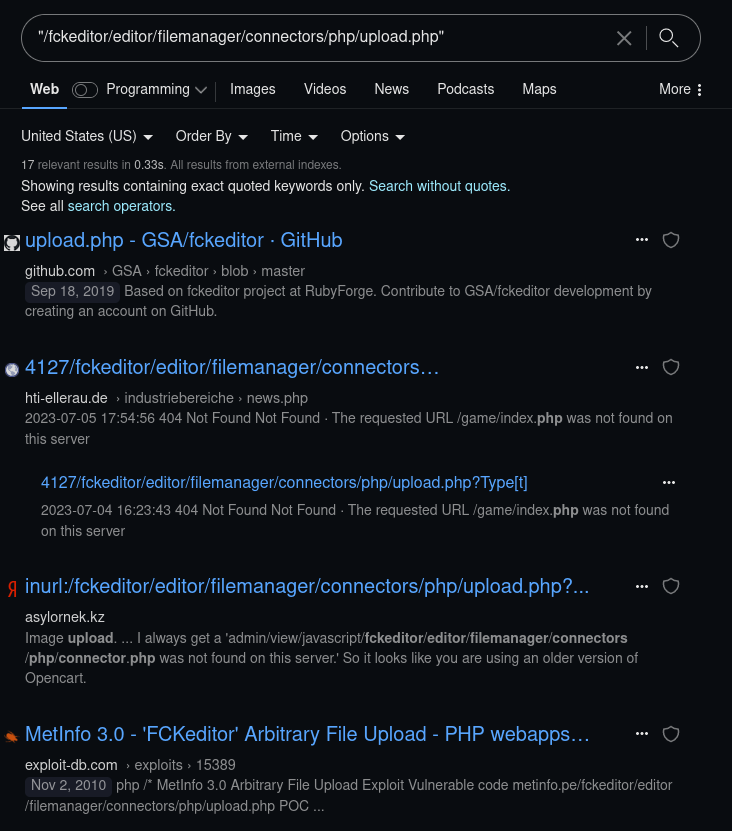
I put the URL in quotes and then search for it. I use Kagi for my searches, so your results may look different if you use something like Google or DuckDuckGo, but not dramatically different. From there, I start digging.
Eventually, when looking through the proof of concept code, firewall log pages and git repos, you’ll get a feel for what the vulnerability is. In this case, it’s CVE-2006-2529.
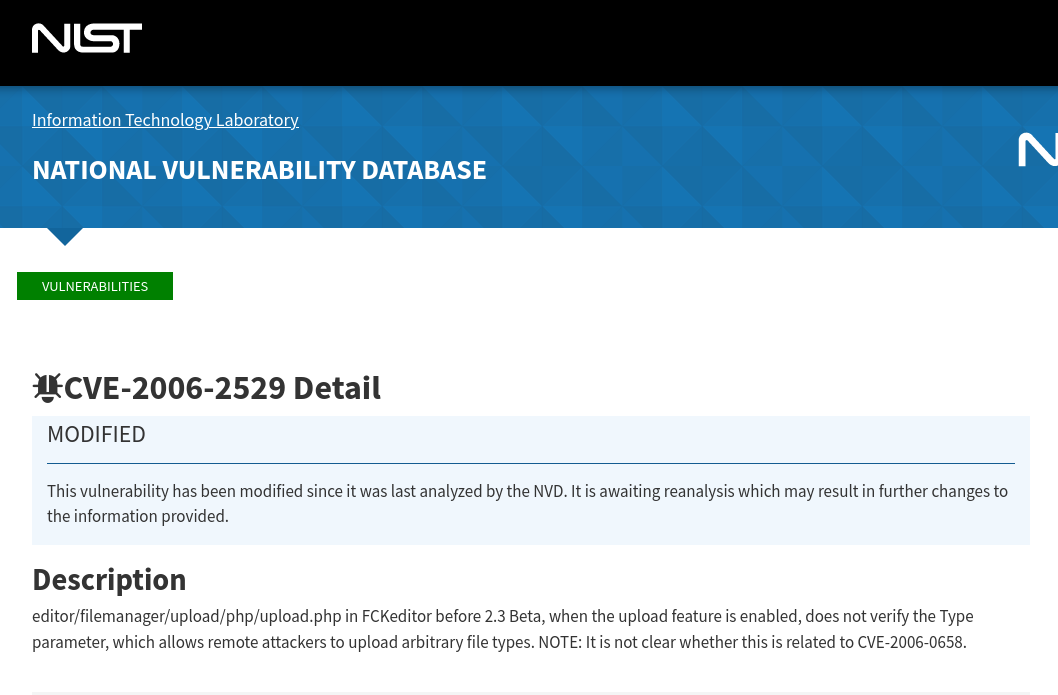
Oooh, this vulnerability was released in 2006, meaning it’s been knocking around since everybody was playing Guitar Hero 2 and trying to get a PERFECT SCORE on Freebird. Neat!
After working backward to find the CVE from the path, I then work forward to find proof of concept code for the CVE. This is good to confirm my findings and also to reference the proof of concept when we make an eventual tag in case the CVE page doesn’t have valid references, or if the vulnerability in question does not have a CVE associated with it. After a bit of finagling, I found this!
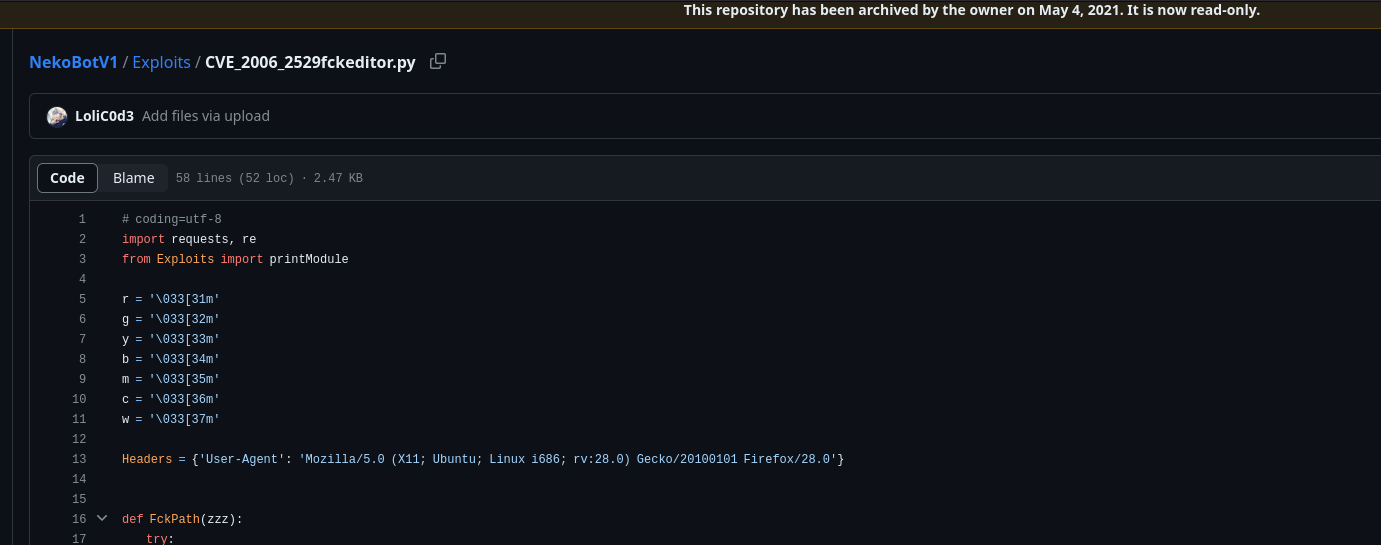
…Or I can just read comments from my coworkers telling me what they’ve found :)
From there, it’s just a matter of writing out the tag. That’s a bit of secret sauce, but the end result looks nice:
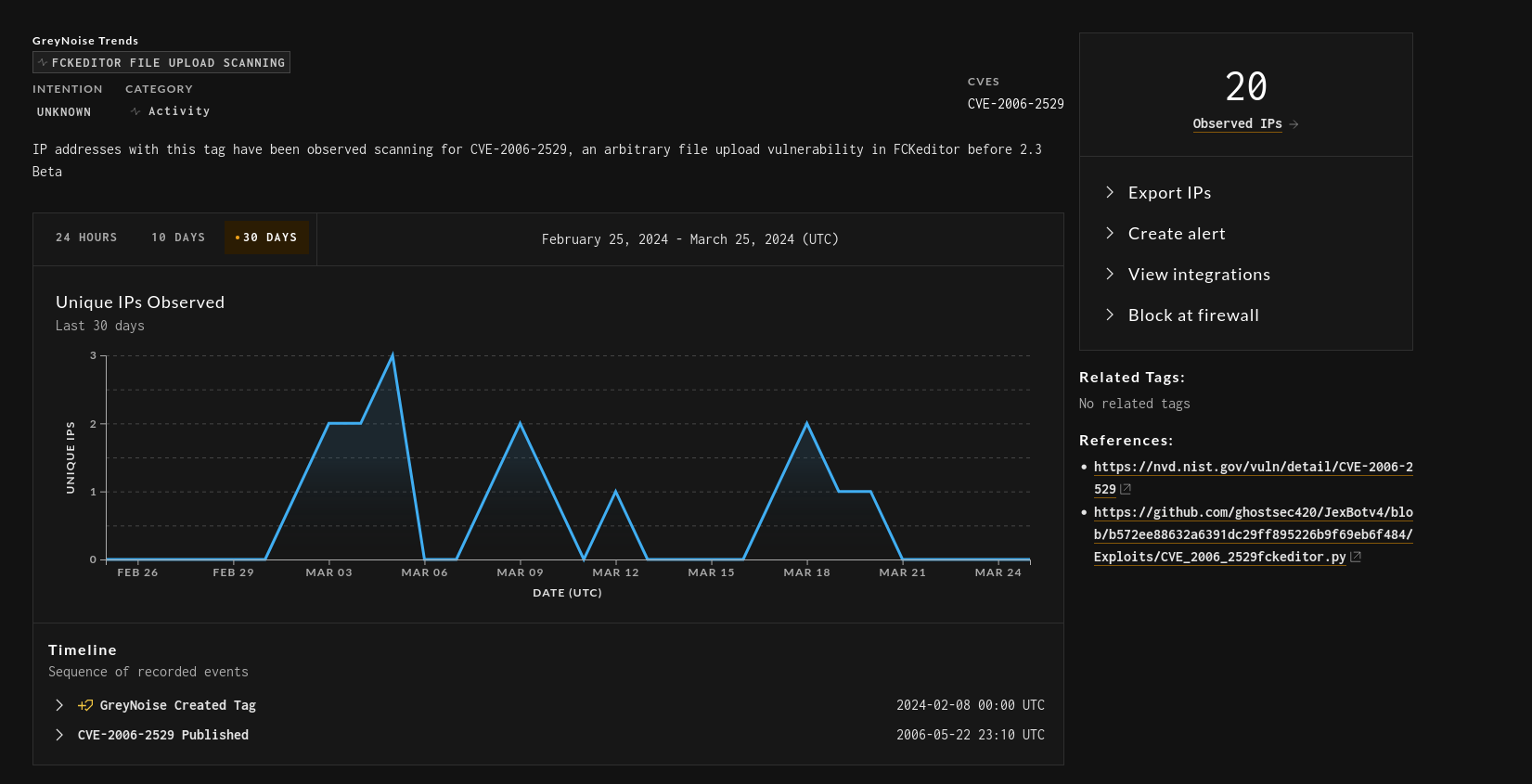
Lather, rinse, repeat with each vulnerability we find in Sift, and the result is a tag database that not only shows the latest and greatest celebrity hacks, but also the old and obscure vulnerabilities that are still floating around in the wild.
Oh, and keep your eyes peeled in April for news about Sift. 👀