Introduction
In this post, I’m going to go over my usage of GreyNoise’s dynamic honeypots to catch a newer proof of concept (PoC) for CVE-2023-47246, and talk a bit more in-depth on why having reactive honeypots is vital to having correct, reliable, and verbose packet captures (PCAP) at this moment.
A Little Background
It was in just the second week of November that SysAid announced CVE-2023-47246, a path traversal vulnerability leading to remote code execution in SysAid On-Premise versions before 23.3.36. SysAid released a helpful advisory blog outlining some integral details on how this vulnerability may be tracked and mitigated for current SysAid users. A couple of days later. Huntress published an even further deep dive, which outlined the root cause and attack vector:
The vulnerability exists in the
doPostmethod within the SysAidcom.ilient.server.UserEntryclass. By injecting a path traversal into theaccountIDparameter and supplying a zlib compressed WAR file webshell as the POST request body, an attacker can control where this webshell is written on the vulnerable server. The attacker can then request the webshell by browsing to the URL where it now resides to gain access to the server.
However, the source code for this PoC was not yet provided. Without PCAP or PoC as concrete evidence of this exploit’s appearance, we can not reliably tag it. In the meantime, we’re left with two courses of action:
- Research and develop our own PoC.
- Set up a SysAid On-Premise honeypot… and wait.
- There’s also the secret third option, where we just use the details disclosed to try and catch something similar, but that’s tangential to this blog.
The first option is actively time-consuming, and would require a member of the research team to drop whatever else they’re working on until they can find a PoC. The second option is passively time consuming. A couple of minutes are invested in setting up the honeypot. However, when a PoC hits the internet, we will be ready and listening.
Suffice to say, I chose the second option.
Why Dynamic Honeypots?
The threat landscape has evolved such that having responsive honeypots that are also capable of impersonating any internet facing software is a must when actually trying to capture the latest exploits. Why is this, though?
For starters, accurately tracking any multistep exploit becomes out of the question without the use of a honeypot capable of responding to each request. At first, this may read as obvious, but there’s actually a bit of subtlety to this. The attacks missed by non-reactive honeypots are not limited to request forgeries. In many cases, getting a session token or cookie is just the first step. This, coupled with potential versioning checks based on the server’s default response, are all reasonable things to expect as the first move in any modern exploit.
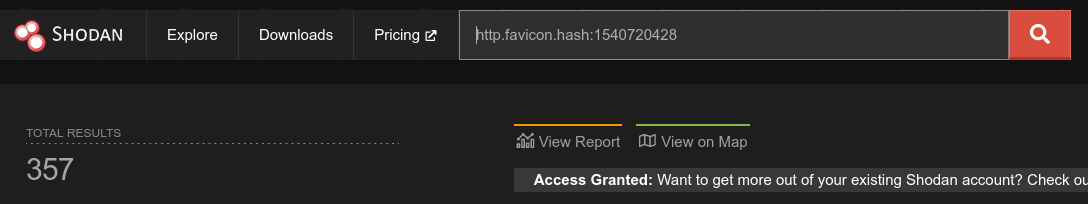
Then, of course, shodan has made it such that targeted exploitation is easier than ever. With just http.favicon.hash:1540720428 as a simple query, I can instantly get a list of 357 potentially vulnerable machines at the time of writing this.
For the most part, attackers are no longer wasting time and making a bunch of noise, spraying and praying an exploit at the entire internet.
The Proof in The Pudding 🍮🧐
This blog was fully inspired by the discrepency between the data seen from a GreyNoise sensor mimicking a vulnerable version of SysAid On-Premise, and the data seen from a generic sensor either imitating a different software or just listening. About two weeks ago I began to see the following payload:
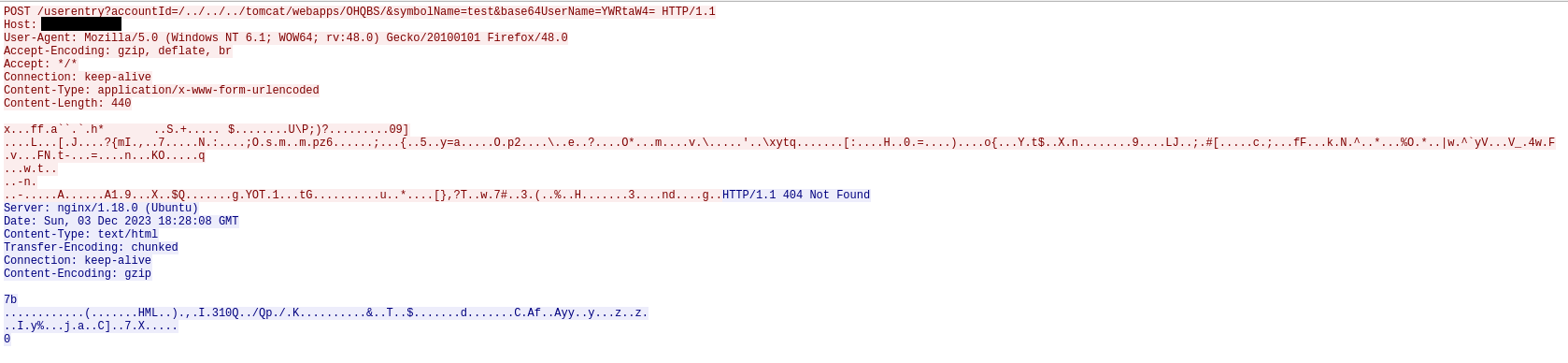
When searching for this within the larger GreyNoise data set it was nowhere to be found… for now. ;) Upon further research, I discovered this PoC was released by W01fh4cker on GitHub at the time of the sensor hits, which appears to be the source of the traffic.
Now, with the given data, a tag can be written!
Conclusion
As attacks evolve, so too should our defense. In order to continue to gain dependable actionable intelligence, the usage of honeypots capable of mimicking multiple steps of a vulnerable software’s response to an exploit chain has become necessary. One of the wonderful things about being a Researcher at GreyNoise is having access to these powerful honeypots and our own curated pcap feeds. Fortunately, GreyNoise has made deploying such sensors easier and more approachable than ever. You can find out more about deploying your own GreyNoise sensor, and see what our sensors are hearing over at viz.greynoise.io!